Find out what the dark web is, how it works, and the security risks it poses to businesses, such as data breaches and exposing credentials.
Table Of Content
- What Is the Dark Web?
- Surface Web
- Deep Web
- Dark Web
- How the Dark Web Works
- Hidden Services
- How to Get to Dark Web Marketplaces
- Legal vs. Illegal Activities on the Dark Web
- Uses that are legal
- Uses that are legal
- Why the Dark Web is Important for Cybersecurity
- Data breaches and passwords that get out
- Selling malware and exploit kits
- Selling access to a corporate network
- Stealing someone’s identity and committing financial fraud
- Signs of an insider threat
- Dark Web Threats to Organizations
- Exposing Employee Credentials
- Leaked Confidential Documents
- Sensitive Personal Data of Customers
- Stolen Intellectual Property
- Before the Attack, Reconnaissance
- Monitoring the Dark Web and Threat Intelligence
- Why It’s Important to Keep an Eye on Things
- How Monitoring Works
- How Threat Intelligence Teams Use Dark Web Insights
- How to Keep Your Business Safe
- Make Identity and Access Management stronger
- Make your passwords safer
- Ongoing Monitoring
- Training for employees to be aware
- Strong planning for responding to incidents
- Regularly managing vulnerabilities
- Data Minimization and Encryption
- Is Dark Web Monitoring Necessary?
Key Takeaways
- The dark web is a secret part of the internet that you can only get to with tools that keep your identity hidden, like Tor.
- It has both legal uses and big illegal markets.
- The dark web makes cybersecurity risks worse for businesses by allowing data theft, credential leaks, malware sales, and insider threats.
- Monitoring the dark web and gathering threat intelligence are important ways to see new threats.
- To lower risk, businesses should use strong access controls, train their employees, keep an eye on things all the time, and have a strong incident response plan.
Dark Web and Its Cybersecurity Risk
Cybersecurity teams around the world are now paying a lot of attention to the dark web, which used to be a small part of the internet. People often think of it as a dark place full of criminals, but that’s not the whole story. There are both legitimate privacy-focused activities and a thriving underground economy based on cybercrime on the dark web. To lower risk and improve information security programs, businesses of all sizes need to know how the dark web works and how it leads to threats in the real world.
This guide tells you what the dark web is, how it works, why it’s important, and what businesses can do to stay safe from cybersecurity threats that come from it.
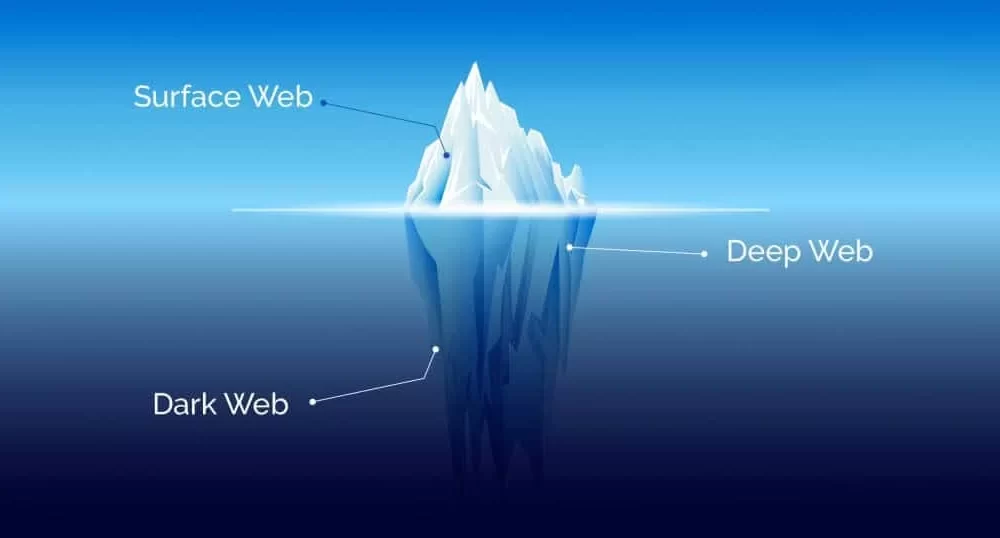
What Is the Dark Web?
You can’t get to the dark web with regular browsers like Chrome, Safari, or Firefox. It’s a small, hidden part of the internet. Instead, it needs special software, like the Tor browser, which sends traffic through layers of encryption to hide the user’s identity and location.

It’s helpful to know what makes the dark web different from other parts of the internet:
Surface Web
Search engines index this part of the internet that anyone can access. This is where news sites, social media sites, and online stores all belong.
Deep Web
This includes things like online banking pages, academic databases, intranet systems, and subscription-based content that search engines don’t index.
Dark Web
The dark web is a part of the deep web that is hidden on purpose and can only be reached with tools that keep your identity secret. Criminals like it because it’s anonymous, but so do people who need privacy, like whistleblowers or dissidents.
In essence:
Surface Web = searchable
Deep Web = private but open to everyone.
Dark Web = hidden and private
How the Dark Web Works
Tor (The Onion Router) is one of the most well-known technologies that help keep people anonymous on the dark web. Tor sends a user’s traffic through many volunteer-run servers, or “nodes,” and encrypts each layer, which is similar to how an onion works. It is very hard to find out where a connection came from because of this.
Hidden Services
.onion domains are used by websites on the dark web. These places:
- Search engines don’t index them
- Regular browsers can’t get to it
- Are hosted without giving your name
How to Get to Dark Web Marketplaces
To get to dark web forums or marketplaces, a user usually:
- Sets up Tor finds the .onion address, usually through directories or forums.
- Connects through Tor and uses cryptocurrency to make payments
The anonymity draws in illegal trade, but it also helps people talk to each other in places where censorship is high.
Legal vs. Illegal Activities on the Dark Web
People often think that everything on the dark web is illegal, but this isn’t true. There are both legal and illegal things going on.
Uses that are legal
- Journalists talking to people who know things
- Human rights activists getting around censorship
- People who want to avoid being watched
- Safe places to blow the whistle (like SecureDrop)
Uses that are legal
But the dark web is more famous for its criminal marketplaces, where bad people trade:
- Data that has been hacked
- Malware
- Kits for ransomware
- Identities that have been stolen
- Access to the corporate network and credit card information
- Fake papers
- Drugs and guns
This growing underground ecosystem is very important to modern cybercrime.
Why the Dark Web is Important for Cybersecurity
The dark web is important for businesses because it makes cybercrime easier, faster, and more profitable. The dark web is where a lot of cyberattacks start or end. It is a place where stolen data is shared, criminals can find new recruits, and tools that make attacks easier and cheaper are sold.
Data breaches and passwords that get out
Hackers often sell the data they steal on dark web forums after breaking into a company. This includes:
- Login information for employees
- Information about customers
- Records of money
- Internal documents that are private
Even small amounts of data, like email/password pairs, can be used to start:
- Attacks that stuff credentials
- Business email compromise (BEC) and account takeovers
Selling malware and exploit kits
The dark web makes it easy for even new people to commit cybercrime. Attackers can buy the following for a small fee:
- Ransomware-as-a-Service (RaaS) and zero-day exploits
- Keyloggers and botnets
- Phishing kits and spyware
This makes it easier for attackers to get in and makes more attacks on businesses.
Selling access to a corporate network
One of the most dangerous things happening right now is the sale of access to corporate systems that has already been hacked. People who threaten sell:
- VPN login information
- Access to RDP
- Cloud infrastructure accounts
- Accounts for privileged users
These access points are often where ransomware attacks start.
Stealing someone’s identity and committing financial fraud
Stolen personal information is used in many types of fraud, such as:
- Applications for loans
- Fraud with credit cards
- Attacks using social engineering
- Scams that pretend to be customer support
Any business that deals with customer data is at risk.
Signs of an insider threat
Unhappy workers might try to sell:
- Documents for internal use
- Property of the mind
- Credentials for access
Finding insider activity on the dark web early can stop big problems from happening.
Dark Web Threats to Organizations
Any business that stores or processes data is at greater risk on the dark web. Some of the biggest threats are:
Exposing Employee Credentials
Employees often use the same passwords on different platforms. Attackers can use their credentials to target corporate accounts if they show up in a data dump on the dark web.
Leaked Confidential Documents
Attackers sometimes upload:
- Notes for the office
- Spreadsheets for money
- Code source
- Logs for customer support
These leaks can hurt your reputation, your finances, and your ability to follow the law.
Sensitive Personal Data of Customers
Customer identity information can be sold over and over again, which keeps the risk of fraud high.
Stolen Intellectual Property
On dark web forums, trade secrets and proprietary technology are worth a lot.
Before the Attack, Reconnaissance
Threat actors often talk to each other about possible targets, such as:
- Servers that are open
- Ports that are easy to hack
- Cloud services that aren’t set up right
- Names and jobs of employees
This information speeds up targeted attacks.
To put it another way, the dark web doesn’t just have cybercrime; it makes it worse.
Monitoring the Dark Web and Threat Intelligence
Dark web monitoring is a proactive cybersecurity practice that keeps an eye on data that has been made public or stolen and is being sold on hidden sites, forums, and marketplaces.
Why It’s Important to Keep an Eye on Things
Monitoring helps businesses:
- Find breaches early
- Find stolen login information
- Stop people from taking over your account
- Find out about attempts to impersonate you
- Keep an eye on insider threats
- Learn how attackers work
- Make incident response stronger
How Monitoring Works
Tools usually:
- Crawl and index sources on the dark web
- Find corporate domains that match the exposed data
- Let security teams know about new leaks.
- Give security analysts context
How Threat Intelligence Teams Use Dark Web Insights
Threat intelligence teams look at activity on the dark web to:
- Look at how your enemy acts
- Make a map of cybercriminal groups
- Figure out how attacks will happen
- Get ready for new threats by making defenses.
This information makes an organization’s ISMS stronger by making sure that protection efforts are in line with real-world threats.
How to Keep Your Business Safe
The dark web is very dangerous, but organizations can greatly lower their risk by using smart cybersecurity controls.
Make Identity and Access Management stronger
- Make sure that strong password rules are followed
- Use multi-factor authentication (MFA)
- Delete accounts that aren’t being used
- Use PAM (privileged access management)
- Follow the rules of least privilege
Make your passwords safer
Employees should learn how to:
- Don’t use the same password twice.
- Don’t use business emails for personal accounts.
- Get a password manager
Ongoing Monitoring
Set up constant access to:
- Credentials that got out
- Forums and sources on the dark web
- Paste sites
- Breach storage areas
Companies that find leaks early can stop the attack chain before it causes a lot of damage.
Training for employees to be aware
One of the most common ways to attack is through human error. Training should include:
- Phishing
- Scamming people online
- Keeping passwords safe
- How to browse safely
Strong planning for responding to incidents
An incident response team that is ready should have:
- Roles and responsibilities that are clear
- Made plans for how to talk to people
- Playbooks for leaking credentials
- How to respond to ransomware
Regularly managing vulnerabilities
Quickly patch known security holes to make them less useful.
Data Minimization and Encryption
Encryption limits the damage even if data is stolen.
Is Dark Web Monitoring Necessary?
Dark web monitoring is not required by standards like ISO 27001, but it is becoming more and more common as a best practice, especially for businesses that:
- Keep private information about customers
- Work in industries with rules
- Are often attacked by hackers
- Use a lot of workers or spread them out
- Have a lot of digital footprints
Some of the benefits are:
- Finding it early
- Less damage from attacks
- More clear threat visibility
- Responding to incidents faster
Some of the limitations are:
- The dark web doesn’t show all data.
- Some sources can’t be trusted
- Cybercriminals move to different platforms all the time.
Monitoring should be one part of a multi-layered cybersecurity plan, not a separate control.



