Discover what ISO 27001 is and why it matters for information security. Learn about its scope, benefits, structure, certification process, and practical implementation insights.
Table Of Content
What is ISO 27001? – Information Security Management System
ISO 27001 is a standard that is recognized around the world for setting up, running, keeping up, and constantly improving an Information Security Management System (ISMS). It gives you a structured way to keep sensitive information safe and deal with information security risks. ISO 27001 is used by businesses all over the world to show that they care about security, build trust with customers, and make sure they follow the rules.

Purpose & Benefits
The main goal of ISO 27001 is to help businesses manage risks to their information assets in a planned and proactive way. Some of the most important benefits are:
- Risk Reduction: Finding, evaluating, and lowering the risk of possible threats to data.
- Regulatory Compliance: Following the rules and laws about information security that are in place.
- Business Trust: Building trust and a good reputation with clients, partners, and other stakeholders.
- Operational Efficiency: Making security processes more efficient and better managing risks overall.
Scope
ISO 27001 is for businesses of all sizes and in all fields. It covers the whole life cycle of an ISMS, from assessing risks and putting controls in place to monitoring, reviewing, and making improvements all the time. The standard makes sure that businesses always and effectively protect the privacy, integrity, and availability of their data.
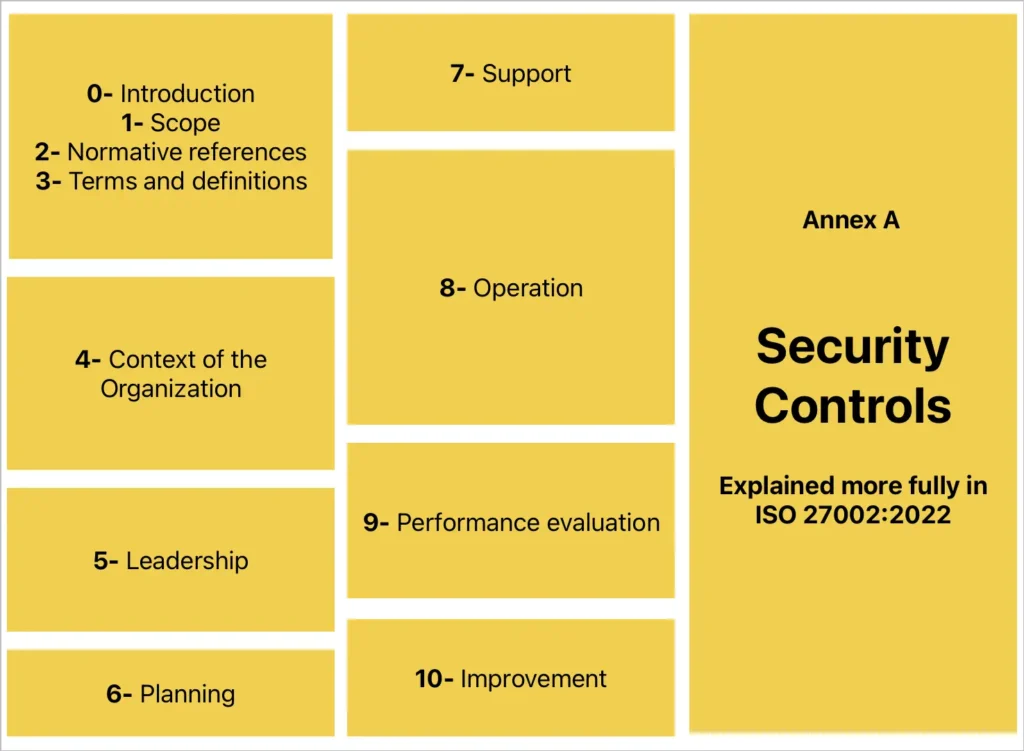
Structure
ISO 27001 has a list of 114 controls organized into 14 domains in Annex A. These controls are required for an ISMS. Some of the areas these domains cover are:
- Information security policies
- Organization of information security
- Human resource security
- Access control and cryptography
- Physical and environmental security
- Incident management and business continuity
ISO 27002 for controls guidance, ISO 27005 for risk management, and ISO 27004 for metrics and measurement are all part of the larger ISO 27000 family.
Certification Process
Becoming ISO 27001 certified involves several key steps:
- Gap Analysis: Evaluate current security practices against ISO 27001 requirements.
- Implementation: Develop policies, procedures, and controls to meet the standard.
- Internal Audit: Assess readiness and identify areas for improvement.
- Certification Audit: Conducted by an accredited certification body.
- Continual Improvement: Regular monitoring, review, and updates to maintain compliance.
Insights
Putting ISO 27001 into place can be hard because it takes time, money, and ongoing support from management. Some common mistakes are not properly assessing risks, not keeping complete records, or not making sure employees are aware. Organizations should take things one step at a time, get input from important people, and use expert advice when they need it. Following ISO 27001 not only makes sure that you are following the rules, but it also makes your overall information security stronger and gives stakeholders more trust.
ISO and ISO/IEC 27001 are registered trademarks of the International Organization for Standardization (ISO). For official information, visit ISO’s official website





